You are viewing the RapidMiner Deployment documentation for version 9.7 -在这里检查尖吻鲈属t version
Security Overview
This page summarizes the RapidMiner Platform's security aspects, and gives a short recap about the concepts used. To learn more about how to do a specific security or identity related task, please visit the relevant section of theManage Deployment page.
Features
To ensure a secure operation and a smooth user experience across the constantly growing amount of components of the RapidMiner Platform, we have integrated an Identity Provider to our platform. This component (which is an open source product calledKeyCloak) implements the following functionality:
- A common identity provider for all components of the RapidMiner Platform
- Centralized management of users and their various login credentials (passwords, 2FA, tokens)
- Single Sign-On experience for all components
- Fine-grained, role-based authorization management
- Federated Identity with any SAML v2.0 or OAuth2 based Identity Provider
- Federated users with LDAP
- Session and Audit logging
Architecture
The following diagram illustrates our security architecture on a high level, and the KeyCloak component's role in the center of it.
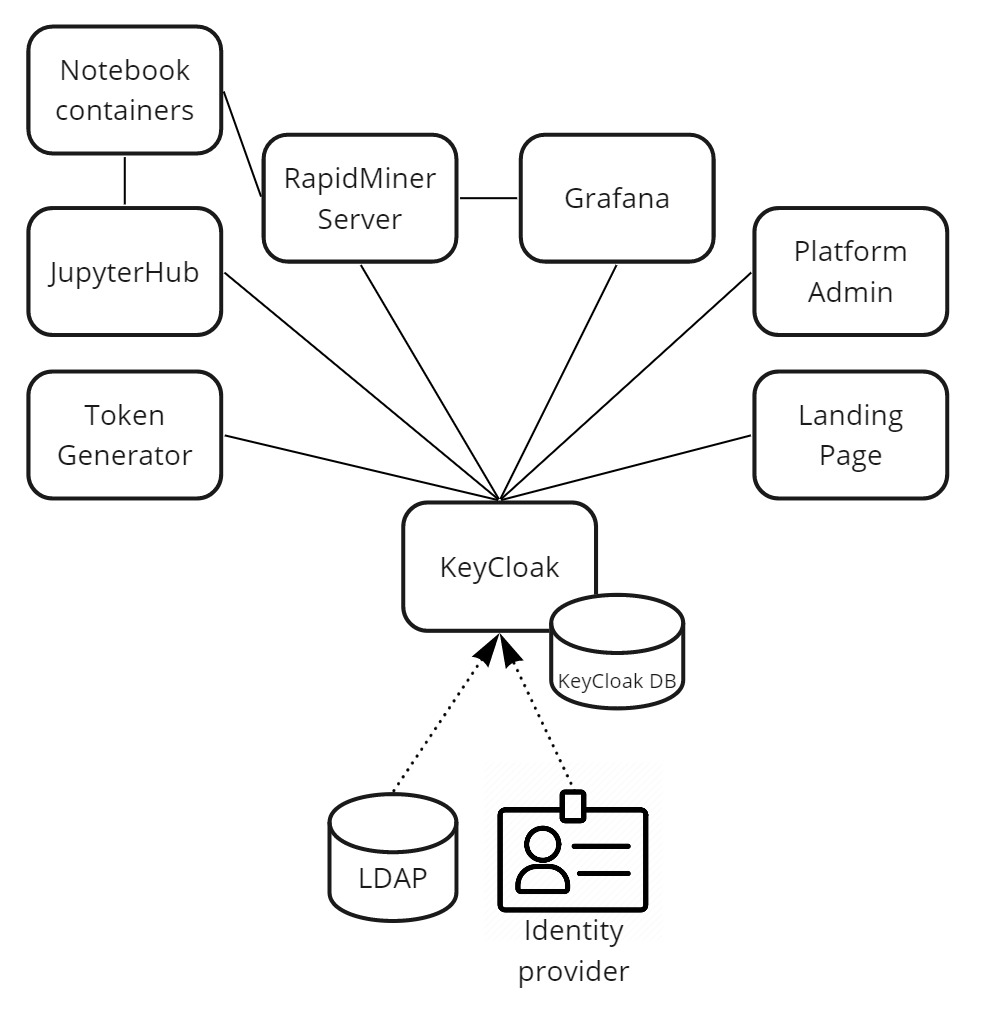
The lines between components represent a relationship where authentication and authorization is happening. The dotted arrows represent optionalidentity and user federationpossibilities.
Authentication and authorization between KeyCloak and other platform components is done using OAuth2/OpenID Connect standards.
Concepts
Using KeyCloak in our Platform Deployment enables us to create elaborate and feature-rich identity and security configuration, but using its management interface can be daunting. It's important to familiarize oneself with the concepts used during configuration. Please refer to theKeyCloak documentationfor an in-depth description.
KeyCloak Configuration
The KeyCloak component is very versatile. We have created a set of default configurations in ourdeployment templatesto help users and admins of the RapidMiner Platform get started quickly. Here we will describe these configuration choices, advise for or against changing them, and provide a link to further guides on how to achieve common administration tasks.
Realm Settings
One realm namedMaster. Should not be renamed or removed. No email correspondence configured, which means no forgot password and verify email flows are enabled by default. Self sign-up is also disabled. Hardened security defenses configured.
Typical administration tasks:
Clients
Deployed components of the RapidMiner Platform appear as Clients in the Master realm. Their client roles are defined according to the needs of each component.
Typical administration tasks:
- Deploying additional platform components (e.g. RapidMiner Go on-prem)
(Realm) Roles
Two composite roles are pre-configured by us:platform-adminandplatform-users. Each is configured to have access to admin functionality or non-privileged user functionality in each deployed component. This is achieved by mapping client roles to these (composite) realm roles.
Typical administration tasks:
Identity Providers and User Federation
None configured by default.
Typical administration tasks:
Authentication flows and Password policies
There is a basic setup pre-configured, involving a username/password prompt and optional Two-Factor Authentication (if set up by the individual user). No password policies are configured by default.
Typical administration tasks:
Groups and Users
No groups are defined by default. There is a user namedadminprovisioned by default, who has theplatform-adminrole. The initial password for the user ischangeit(except forCloud image deployments).
You absolutelyMUSTchange the admin password to ensure a secure operation of your deployment.
Typical administration tasks:
